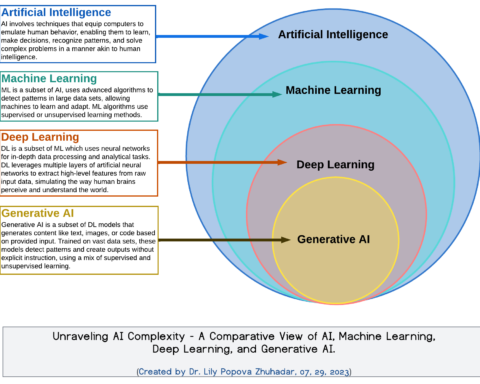
“Machine UnLearning” and “Model Disgorgement” facilitate Art. 17: The Right to Be Forgotten
There’s a phrase from the early years of computer science in the late 1950’s that’s as perrenial as Moore’s Law: “garbage in, garbage out” or GIGO. If the input is rubbish, the output is also bunk. GIGO has plagued programmers for decades but two new areas of research known as “Machine UnLearning” and “Model Disgoregement” are attempting to solve the problem that researchers believe are behind its AI hallucinations or its LLM’s generating factually incorrect information. The Austrian Data Protection