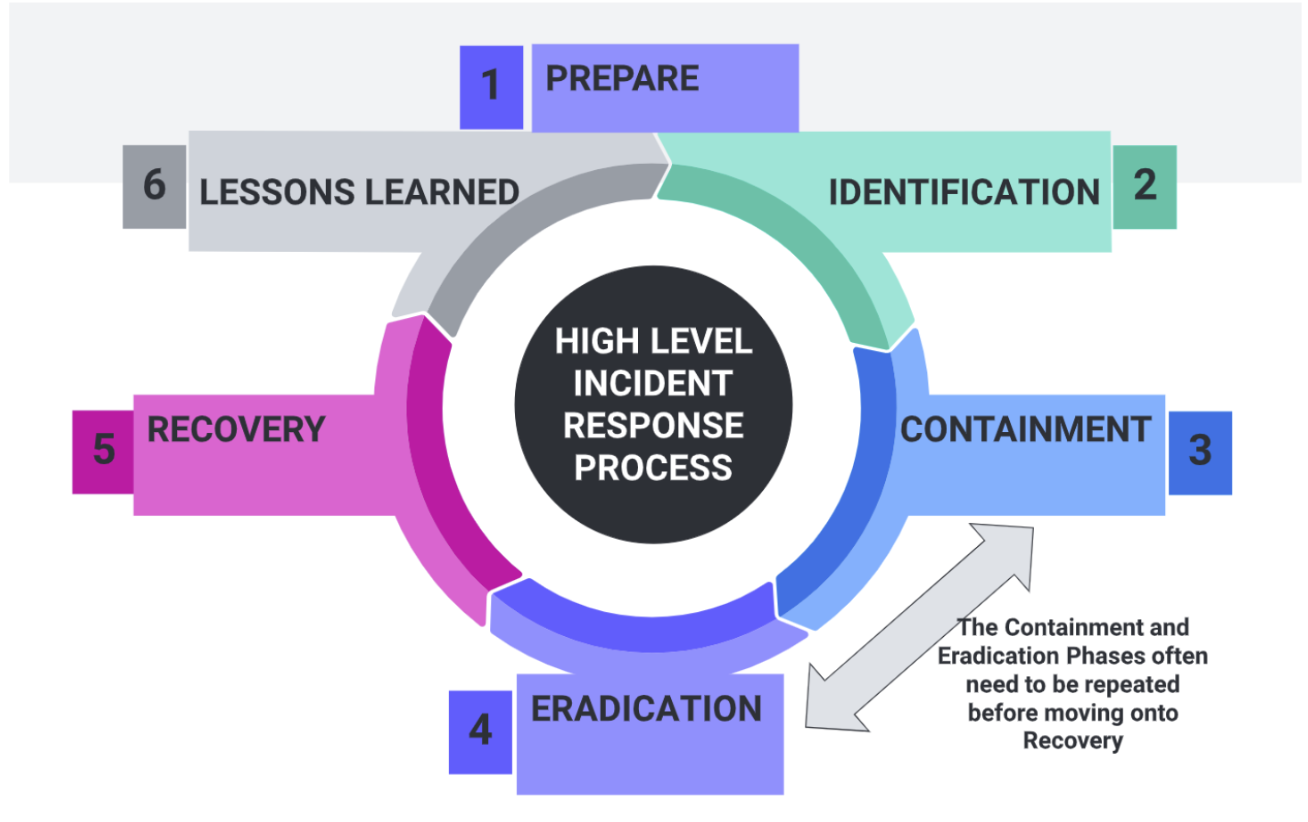
As cybersecurity evolved to confront increasingly sophisticated adversaries and complex attacks, the military company Lockhead Martin published a paper that pioneered concepts such as the cyber kill chain. Hutchins et al proposed that traditional intelligence gathering methods to gain an understanding of the capabilities, actions, and intent of an adversary in war, such as the laying Improvised Explosive Devices by a rival military in urban combat, can also carry over to the cybersecurity domain (Hutchins et al., 2011).
Cyber Threat Intelligence (CTI) has matured in the decade since Lockheed Martin’s Intelligence-Driven Computer Network Defense paper was published but the field retains the aim at its core to more deeply understand the defending organisation’s position in the overall threat landscape with evidence-based knowledge about current and future threats (Mavroeidis & Bromander, 2017). CTI involves collating data such as context, mechanisms, indicators of compromise (IoC), then processing the data into actionable intelligence that identifies, tracks and predicts threat behaviour to inform the security response (Ettinger 2019; Abu et al., 2018). Objectives include improving traceability through continuous monitoring, and implementing countermeasures for the identification, assessment, and management of cyber risk associated with attacks (Hang Thanh Bui et al., 2024). An adversary’s stubborn persistence to cause ongoing damage spurred the aim of moving beyond traditional reactive approaches to cyber security with the objective of becoming more proactive (Girtz, 2021; Barnum, 2014). This creates a resilient security posture for the organisation and ability to make informed decisions (Tatam et al., 2021; Hutchins et al., 2011).
2.a. Cyber Threat Intelligence and organisational security planning
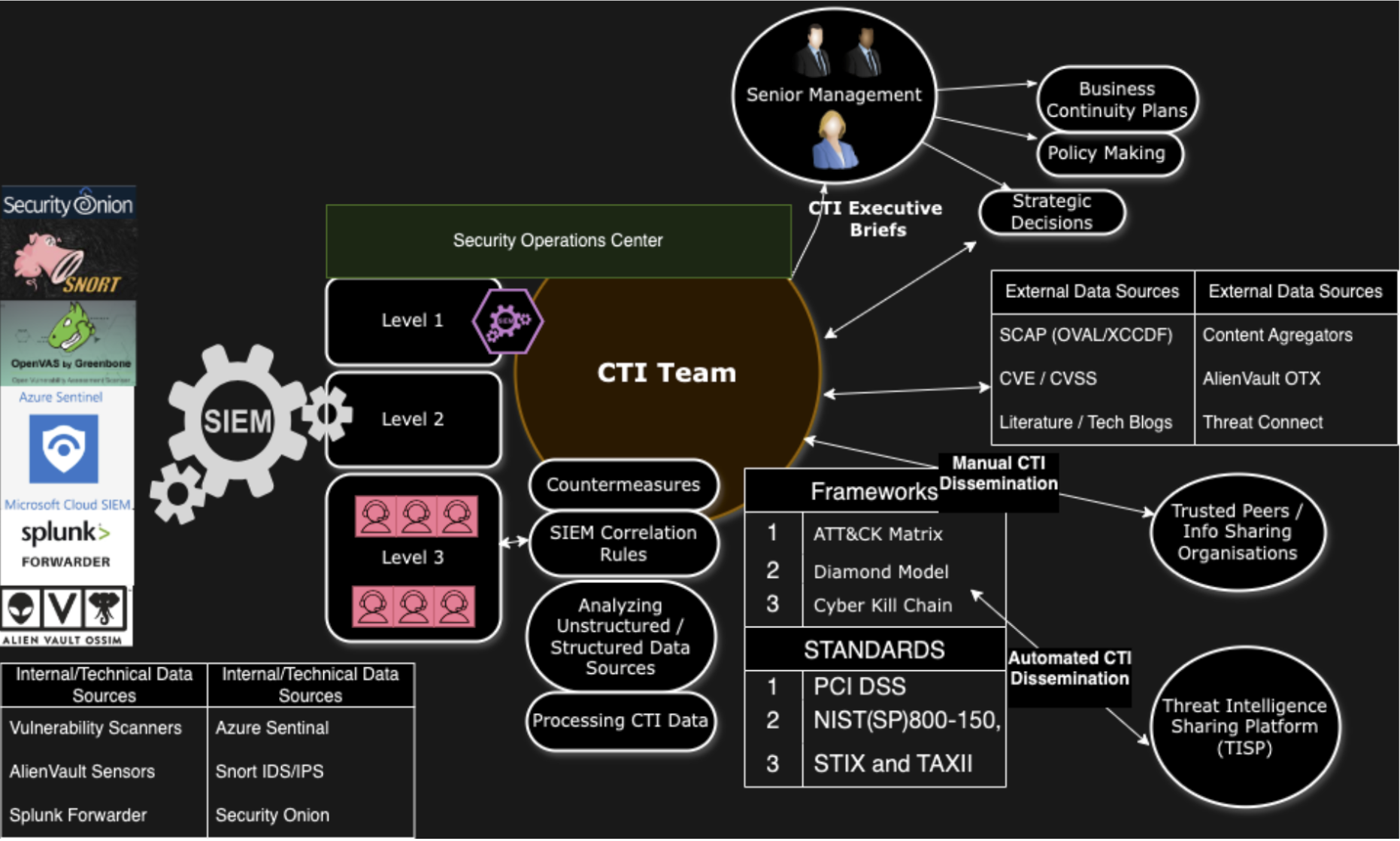
CTI can facilitate a change in organisational security from a reactive state to “proactive, anticipatory and dynamic” (Shin & Lowry, 2020, p. 6). An organisation may adopt CTI inside its existing IT Operations department or develop novel solutions such as so-called CTI-as-a-service which integrates across the organisation in a broader commercial context (Kotsias et al., 2022). CTI agents might also operate at the higher tiers of a L1/L2/L3 Security Operations Center (SOC) whereby Level 1 analysts triage incidents in the Security Information and Event Management (SIEM); Level 2 analysts escalate an incident if it reaches a certain threshold; and Level 3 analysts with higher levels of situational awareness perform CTI on the triaged telemetry data to create actionable intelligence which is disseminated back down the chain to Level 1 (Kotsias et al., 2022). The CTI team may be small but should have significant flexibility to move around the organisation to identify where to focus its efforts to create force-multipliers with actionable intelligence (Girtz, 2021).
2.b. Enhancing security measures with Cyber Threat Intelligence.
CTI enhances the effectiveness of existing security because deploying countermeasures faster than its adversary can evolve to defeat them, raising costs adversaries expend to achieve their objectives (Barnum, 2014). Hutchins et al. made the case that adversaries may attempt numerous intrusions while constantly recalibrating their operations, but a precision strike on the kill chain model meant that just “one mitigation breaks the chain and thwarts the adversary, therefore any repetition by the adversary is a liability that defenders must recognize and leverage” (Hutchins et al., 2011, p. 3). Identifying adversaries inside the company’s network or hosts requires increasing visibility of Indicators of Compromise (IoCs) using existing tools such as SIEM and alerts from IDS/IPS across the network (Tatam et al., 2021). Structured XML-based languages outputted by the Snort IDS can be utilised by STIX (Burger et al., 2014).
- CTI Frameworks
Wagner et al. defined cyber threat frameworks as the universal language of threat intelligence and defence which facilitate collaboration (Wagner et al., 2019). The following are the most popular frameworks used in the CTI field:
- Cyber Kill Chain developed by Lockheed Martin describes the stages of a cyber attack. The kill chain implicitly assumes a unidirectional workflow makes no allowance for an adversary’s retreat during an attack. In contrast, MITRE and Diamond’s models are more dynamic systems allowing for a broader range of adversary behaviours.
- The MITRE ATT&CK specialises in TTPs and provides a matrix. Useful for detailing an adversary’s behaviour but does not provide a linear progression of the attack like the Cyber Kill Chain. ATT&CK and Cyber Kill-Chain were developed after years of observations of APT behaviour (Tatam et al., 2021).
- The Diamond Model specialises in intrusion analysis and breaks down a cyberattack into four elements: the adversary (threat actor), the victim (compromised system), the infrastructure (phishing setup or botnet), and the capability (lateral movement). It does not represent a sequential progression of a cyberattack like Cyber Kill Chain but draws from the scientific method by using the logic that “every cyber event involves an adversary who utilizes a capability over some infrastructure to compromise a victim.” (Dahj, 2022).
- AlienVault was specifically designed to avoid the rigidity of the Lockheed Martin cyber kill chain.
4.a. Threat Intelligence Sharing Platforms (TISPs)
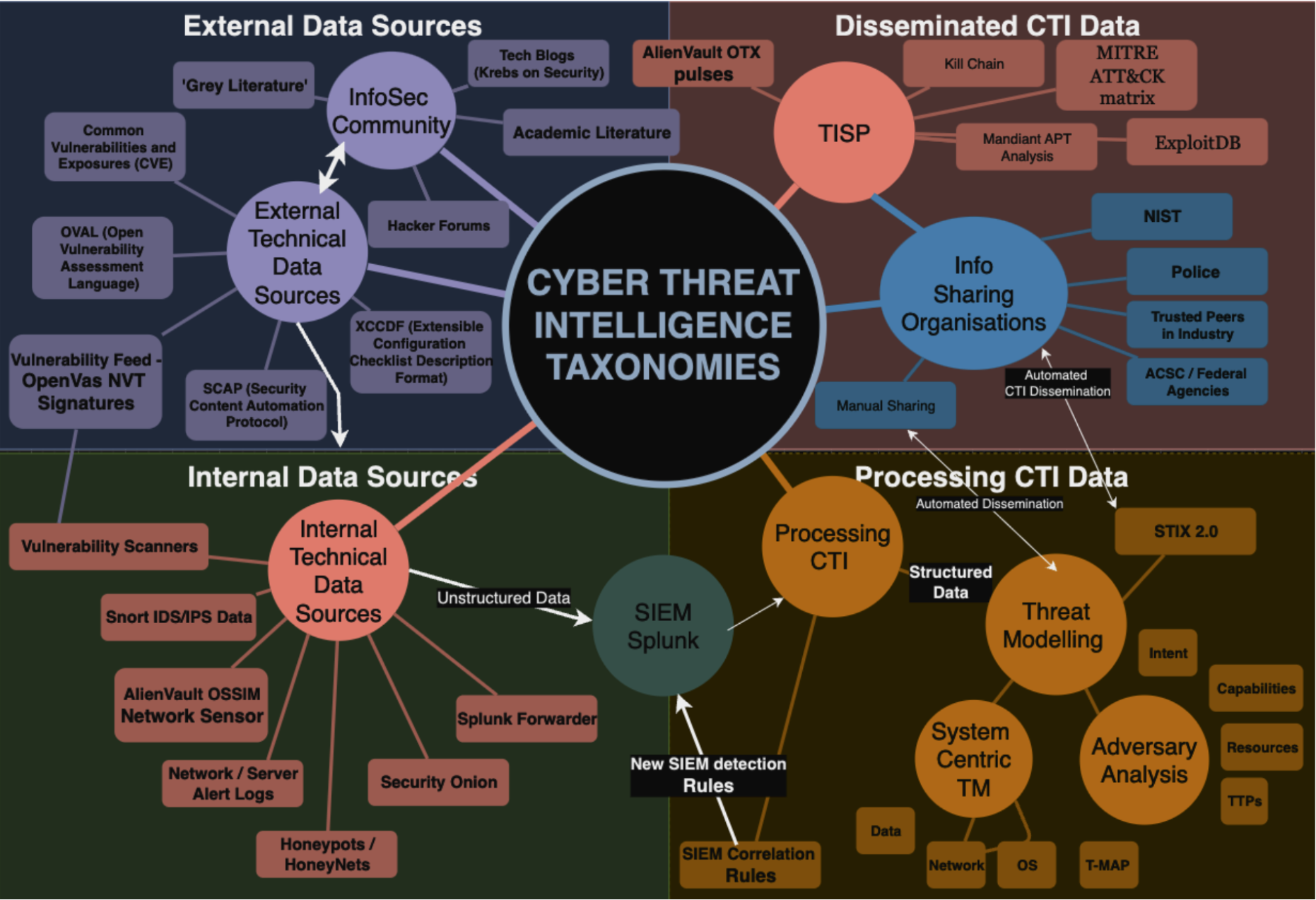
Serrano et al. warned a decade ago of a growing awareness of the need for better information sharing mechanisms from within the cybersecurity community, stating CTI sharing was slow, inefficient, and manually laborious using non-structured data sources (Serrano et al., 2014). The emergence of CTI platforms known as TISPs, however, helped manage data into actionable intelligence (Abu et al., 2018). Abu et al. have divided these TISPs into two categories, Content Aggregation that consolidates threat data feeds including FS-ISAC, OASIS, IBM X-Force Exchange, Facebook Xchange, HP ThreatCentral, Checkpoint IntelliStore, Alienvault OTX, and Crowdstrike. TISPs geared towards Threat Intelligence Management Systems include Intelworks, Soltra, Threatstream, ThreatConnect, Vorstack, ThreatQuotient.
4.b. CTI Dissemination Standards
Given the complexities, pace, and quantity of data involved in CTI dissemination, automation aids human analysis but standardised and structured data is needed from the widest range of sources to leverage the information (Barnum, 2014). The OASIS CTI Technical committee defined TAXII and STIX as “standardized data representations and protocols designed to address the need to model, analyze, and share cyber threat intelligence”. STIX’ structure facilitates storage, analysis, and dissemination automation process, with a standardised language for cyber observables, indicators, incidents, adversary tactics, exploits, and courses of action. TAXII is compatible with STIX and enables peer-to-peer sharing of CTI data “across product lines, services, and organisational boundaries.” (Gong, 2018, pp. 667-669). TAXII also defines protocols and data formats for securely exchanging cyber threat information for the detection, prevention, and mitigation of cyber threats in real time (Davidson & Schmidt, 2012).
Davidson & Schmidt believe the STIX and TAXII standards create the greatest level of interoperability for effectively sharing CTI data. In 2013, Open IoC sought to address a challenge to investigators when describing an adversary’s “activity, utilities, malware, and other Indicators of Compromise” by creating the OpenIOC format which standardised terms and taxonomy when describing malware artefacts discovered during Incident Response (Gibb & Kerr, 2013, p. 1). Furthermore, Barnum documented the increasing trend of machine-t0-machine transfer of simple datasets during the dissemination process, including REN-ISAC’s Security Event System and its Collective Intelligence Framework component, the state of Washington’s PRISEM, AbuseHelper. (Barnum, 2014). NIST also developed a standard for CTI dissemination (Johnson et al., 2017).
- Tailoring CTI Strategy
A company’s CTI strategy can be tailored by deciding how much information it is willing to share with trusted organisations. A challenge to intelligence sharing has always been a reluctance to share network data, such as Indicators of Compromise (IoC), because they believe it may make them more vulnerable. An organisation can decide what actions to take at the strategic, operational and tactical levels when using CTI on current and emerging threats (Abu et al., 2018). CTI helps senior management understand the threat landscape, make informed decisions, and chart strategic solutions to mitigate risk exposure (Kotsias et al., 2022). Strategic decisions include whether to share CTI data manually or automate the process despite the lack of models and tools that made it challenging (Vázquez et al., 2024).
Manual sharing of CTI data between organisations where a trusted relationship already exists is widely performed but may be ineffective for reasons such as slow speed, human error when processing data, as well as subjective relevance filtering (Wagner et al., 2019). Decision makers establish predefined policies about what CTI data is disseminated, actions to be initiated when an incident is detected, and “how it should be handled based on agreed frameworks of trust in such a way as to maintain appropriate levels of consistency, context and control.” (Barnum, 2014, p. 11). If CTI determines an adversary’s TTPs include spear phishing to target the company’s finance department, a strategic decision may include mandating cyber awareness training and phishing simulations. Ultimately, CTI decision-making is contingent on the quality of QTI against criteria discussed in section 7.b. on data sources below (Kotsias et al., 2022).
6.a. Threat Modelling (TM)
TM is the process where potential security vulnerabilities and their associated level of risk are identified so that they can be mitigated in a targeted manner (Tatam et al., 2021). Hang Thanh Bui et al. identified three primary questions that threat modelling seeks to address, “What are the primary vulnerabilities that must be considered?”, “Which component of the system is most susceptible to security breaches?”, and “Where might threats emerge that could compromise the system’s integrity?” (Hang Thanh Bui et al., 2024, p. 5).
TM creates situational awareness to inform decision-makers on threat-related risks, as well as formalises the evaluation of security controls whereby threats are identified in a proactive manner and an asset’s vulnerability in the face of that threat is analysed (Hang Thanh Bui et al, 2024; Tatam et al, 2021). Tatam et al. also state that modelling threats with taxonomic classifications increases visibility of an attack. Defenders can generate metrics of this resiliency by measuring the performance and effectiveness of defensive actions taken against the intruders (Hutchins et al., 2011). TM includes asset-centric, system-centric, threat-centric, and data-centric approaches (Eng, 2017).
6.b Adversary Analysis
Taxonomically classifying attackers, their TTPs and characteristics, while linking them with associated vulnerabilities, give analysts the edge in their defence (Tatam et al., 2021) The analyst seeks to understand the nature of the threat through its detection and by modelling “threat-related actions, behaviours, capabilities, intents, attributed actors, etc” may then discern indicator patterns, suggest a course of action, and share the intel with trusted parties (Barnum, 2014, p. 9). Detecting an adversary’s capabilities in the form of tactics, techniques, and procedures (TTPs); how the TTPs can be mitigated; as well as identifying the adversaries, where they come from, and what they seek to achieve can facilitate the elimination of threats earlier (Barnum, 2014).
7.a. Data Sources
The AlienVault surveyed Black Hat 2016 attendees and discovered most participants rely on internal detection processes as CTI data sources such as email log, SIEM alerts, IDS/IPS event logs, DNS logs, firewall logs, etc. Of the external CTI data sources, 48% of respondents used sources from trusted peers; 44% percent utilised paid subscription services; 38% from government agencies; and 37% from crowdsourced OSINT.
Hang Thanh Bui et al. document technical data sources including unstructured sources which “categorises relevant cyber threats and vulnerabilities without a standard format such as Hacker Forums (AntiChat, AntiOnline), Social Media (Twitter, Facebook etc.), Honeypots, Unstructured (CTI Reports), Blogs (KrebsonSecurity), clear web, Security Websites (AlienVault, SecurityList), Dark Web such as DarknetMarketplace (DNMs).” Structured data sources include threat and vulnerability databases with standardised formats such as “CTI feeds (in STIX format), Common Vulnerabilities and Exposures (CVE), National Vulnerability Database (NVD), MITRE ATT&CK matrix, Web Repositories (Github, Seebug, ExploitDB, PacketStorm), Network/Server Logs”. (Hang Thanh Bui et al., 2024, p. 8). SIEM rules must create correlations between an adversary’s TTPs and suspected Indicators of Compromise. Combining low-level IoC’s to give a birds eye view of attack patterns can be essential in the identification of an APT campaign (Tatam et al., 2021).
7.b. Reliability and Relevance
Europe’s peak cybersecurity body set down best practices for the dissemination and usage of CTI, stating that for threat information to be actionable it must have the following attributes: trust, reputation, relevance, anonymity, timeliness, and data interoperability (European Union Agency for Cybersecurity, 2015). Of the aforementioned attributes, Wagner et al. state that the most important pillar of an information sharing program is trust.
When the goal is to create situational awareness between information sharing organisations on potential threats and adversaries, automating the process of CTI sharing is beneficial and can be done over trusted groups and platforms such as the Information Sharing and Analysis Center (ISAC), AlienVault, Cyber Security Information Sharing Partnership (CiSP) in the UK.
CTI professionals need a broad awareness about what is happening in their industry to understand the threat landscape. This means it’s wise to use a wide range of sources from academic papers to so-called ‘grey literature’ including CERT whitepapers, software vulnerability reports, public information sharing platforms, and tech blogs from industry leaders in your field (Abu et al., 2018). However, Abu et al. state that differentiating between actionable intelligence and useless noise is also a challenge when assessing the reliability and relevance of CTI platforms.
Following the guidelines set by Kitchenham and Charters, Hang Thanh Bui et al. listed the following electronic data sources including IEEE, ACM and Web of Science, the Scopus database and the Google Scholar search engine to stay abreast of emerging threats in the field (Hang Thanh Bui et al., 2024). The availability of CTI sources continues to increase but there is “a lack of a comprehensive CTI source with specific features that can be extracted for a specific purpose.” (Hang Thanh Bui et al., 2024, p. 8). Kotsias et al. noted the CTI adopting the U.S. Army’s Keystone Manual for Military Intelligence in the nine criteria to judge reliability and relevance: accuracy, relevancy, completeness, precision, timeliness, usability, reliability, predictiveness, tailorability (Kotsias et al., 2022).
The history of computing is intertwined with military research, from DARPA inventing the early internet to create redundancy against bombing campaigns to cybersecurity strategies such as Defence-in-Depth adopting military stratagems practised since the late Roman Empire. CTI has matured since Lockheed Martin’s Intelligence-Driven Computer Network Defense paper introduced the cyber kill chain, but as adversaries also evolve with the times, Shin & Lowry are correct to cite Sun Tzu’s ancient battlefield wisdom from the Art of War, “If you know the enemy and know yourself, you need not fear the result of a hundred battles.”
References
Abu, M. S., Selamat, S. R., Ariffin, A., & Yusof, R. (2018, April). Cyber Threat Intelligence – Issue and Challenges . Indonesian Journal of Electrical Engineering and Computer Science . https://www.researchgate.net/publication/322939485_Cyber_Threat_Intelligence_-_Issue_and_Challenges. pp. 371~379.
Barnum, S. (2014). Standardizing Cyber Threat Intelligence Information with the Structured Threat Information eXpression (STIXTM). https://stixproject.github.io/about/STIX_Whitepaper_v1.1.pdf
Bassog, L. (2024). Identifying the Problems With the Data Analysis Stage of Cyber Threat Intelligence (CTI) Process and Possible Solutions – ProQuest. Proquest.com. https://www.proquest.com/openview/8deee2ab33bf6de1dc875be9278eb7ee/1?pq-origsite=gscholar&cbl=18750&diss=y
Burger, E. W., Goodman, M. D., Kampanakis, P., & Zhu, K. A. (2014). Taxonomy Model for Cyber Threat Intelligence Information Exchange Technologies. Proceedings of the 2014 ACM Workshop on Information Sharing & Collaborative Security – WISCS ’14. https://doi.org/10.1145/2663876.2663883
Dahj, J. N. M. (2022). Mastering cyber intelligence : gain comprehensive knowledge and skills to conduct threat intelligence for effective system defense. Packt Publishing, Limited.
Davidson, M., & Schmidt, C. (2012). The TAXII XML Message Binding Specification Version 1.0 (draft). https://taxii.mitre.org/specifications/version1.0_draft1/TAXII_Services_Specification_1.0_Draft.pdf
Eng, D. (2017). Integrated Threat Modelling. Duo.uio.no. http://hdl.handle.net/10852/55699
Ettinger, J., Barmer, H., Kane, J., Brandon, E., Mellinger, A., & Evans, H. (2019, May 22). Cyber Intelligence Tradecraft Report: The State of Cyber Intelligence Practices in the United States (Study Report Only). SEI Digital Library. https://insights.sei.cmu.edu/library/cyber-intelligence-tradecraft-report-the-state-of-cyber-intelligence-practices-in-the-united-states-study-report-only/
European Union Agency for Cybersecurity. (2015). Actionable information for security incident response – Publications Office of the EU. Publications Office of the EU. https://op.europa.eu/en/publication-detail/-/publication/b25e3fc5-112a-49ef-86cd-c2ea191cdd94/language-en
Gibb, W., & Kerr, D. (2013, October). OpenIOC: Back to the Basics | Mandiant. Google Cloud Blog; Google Cloud. https://cloud.google.com/blog/topics/threat-intelligence/openioc-basics/
Girtz, C. (2021). Optimising cyber threat intelligence for your organisation. Cyber Security: A Peer-Reviewed Journal, 5(2), 135–141. https://www.ingentaconnect.com/content/hsp/jcs/2021/00000005/00000002/art00005
Gong, N. (2018). Barriers to Adopting Interoperability Standards for Cyber Threat Intelligence Sharing: An Exploratory Study. Intelligent Computing, 2, 666–684. https://doi.org/10.1007/978-3-030-01177-2_49
Hang Thanh Bui, Hamed Aboutorab, Arash Mahboubi, Gao, Y., Nazatul Haque Sultan, Chauhan, A., Mohammad Zavid Parvez, Bewong, M., Islam, R., Islam, Z., Camtepe, S. A., Praveen Gauravaram, Singh, D., M. Ali Babar, & Yan, S. (2024). Agriculture 4.0 and Beyond: Evaluating Cyber Threat Intelligence Sources and Techniques in Smart Farming Ecosystems. Computers & Security, 140, 103754–103754. https://doi.org/10.1016/j.cose.2024.103754
Hutchins, E., Cloppert, M., & Amin, R. (2011). Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains. https://www.lockheedmartin.com/content/dam/lockheed-martin/rms/documents/cyber/LM-White-Paper-Intel-Driven-Defense.pdf
Johnson, C. S., Feldman, L., & Witte, G. A. (2017). Cyber Threat Intelligence and Information Sharing. NIST. https://www.nist.gov/publications/cyber-threat-intelligence-and-information-sharing
Kotsias, J., Ahmad, A., & Scheepers, R. (2022). Adopting and Integrating Cyber-Threat Intelligence in a Commercial Organisation. European Journal of Information Systems, 32(1), 1–17. https://doi.org/10.1080/0960085x.2022.2088414
Mavroeidis, V., & Bromander, S. (2017, September 1). Cyber Threat Intelligence Model: An Evaluation of Taxonomies, Sharing Standards, and Ontologies within Cyber Threat Intelligence. IEEE Xplore. https://doi.org/10.1109/EISIC.2017.20
Meszaros, J., & Buchalcevova, A. (2017). Introducing OSSF: A framework for online service cybersecurity risk management. Computers & Security, 65, 300–313. https://doi.org/10.1016/j.cose.2016.12.008
Serrano, O., Dandurand, L., & Brown, S. (2014). On the Design of a Cyber Security Data Sharing System. Proceedings of the 2014 ACM Workshop on Information Sharing & Collaborative Security – WISCS ’14. https://doi.org/10.1145/2663876.2663882
Shin, B., & Lowry, P. B. (2020). A review and theoretical explanation of the “Cyberthreat-Intelligence (CTI) capability” that needs to be fostered in information security practitioners and how this can be accomplished. Computers & Security, 92, 101761. https://doi.org/10.1016/j.cose.2020.101761
Tatam, M., Shanmugam, B., Azam, S., & Kannoorpatti, K. (2021). A review of threat modelling approaches for APT-style attacks. Heliyon, 7(1), e05969. https://doi.org/10.1016/j.heliyon.2021.e05969
Tzu, S., & Minford, J. (2002). The Art of War. New England Review (1990-), 23(3), 5–28. https://www.jstor.org/stable/40244134
Vázquez, D. F., Acosta, O. P., Spirito, C., Brown;, S., & Reid, E. (2024). Conceptual framework for cyber defense information sharing within trust relationships. Ieee.org. https://ieeexplore.ieee.org/abstract/document/6243990/
Wagner, T. D., Mahbub, K., Palomar, E., & Abdallah, A. E. (2019). Cyber threat intelligence sharing: Survey and research directions. Computers & Security, 87(0167-4048), 101589. https://doi.org/10.1016/j.cose.2019.101589