Some terminology cheat sheets for the Security+ cert to get your head around the concepts and vocab. I can highly recommend the study materials and practice tests from Dion Training.
LEGISLATION SECURITY+ CHEAT SHEET
The Sarbanes-Oxley Act is a US legislation that mandates various practices to protect investors by improving the accuracy and reliability of corporate financial statements and disclosures.
The Computer Security Act (1987) focuses on the security of federal computer systems processing confidential information, it does not deal with financial reporting transparency.
FISMA (Federal Information Security Management Act) aims to govern the security of data processed by federal government agencies, but it doesn’t specifically focus on financial transparency and accountability.
GDPR (General Data Protection Regulation) is a European Union regulation that pertains to the protection of personal data and its processing, ensuring that entities collect and use such data fairly and transparently.
FIPS (Federal Information Processing Standards) are standards that provide important guidelines and requirements for cryptography used to secure federal information systems, except those related to national security.
While ISO/IEC 27001 is an important standard for information security management systems, it does not set specific requirements for cryptographic modules within federal computer systems.
PCI DSS relates to the protection of cardholder data and is not focused on the cryptographic requirements for federal information systems. This publication provides guidelines for digital identity but does not specify requirements for cryptographic modules within federal systems.
DATA SECURITY+ CHEAT SHEETS
The DATA CONTROLLER is an entity or person who determines the purposes and means of processing personal data. They have overall responsibility for ensuring that data processing is carried out in compliance with applicable privacy laws and regulations.
DATA CUSTODIAN The organization that handles data retention and storage is more aligned with a data custodian. A data custodian is responsible for the storage, protection, and maintenance of data. They ensure that data is kept secure and accessible to authorized users as required.
DATA SUBJECT The individual whose data is being processed refers to the data subject. The data subject is the individual to whom the personal data belongs, the person to whom the data is collected and processed.
The DATA OWNER is responsible for defining the access policies to data, including who has the authority to access certain information based on their role or department. This role involves making decisions about data access privileges and often overseeing how data is classified and used within the organization.
The DATA PROCESSOR handles personal data on behalf of the Data Controller and according to their instructions. They are involved in the actual processing of data but do not have the authority to make decisions regarding who is allowed to access the data.
CYOD DEVICE SECURITY+ CHEAT SHEET
CYOD stands for Choose Your Own Device, which is a deployment model that allows employees to choose from a list of approved devices provided by the company. This model can offer some flexibility and convenience to the employees, as they can select the device that best suits their needs and preferences. However, this model also enables the company to maintain some security standards and policies on these devices, as it can limit the types and models of devices that are allowed, as well as enforce security configurations and updates on them.
BYOD stands for Bring Your Own Device, which is a deployment model that allows employees to use their personal devices, such as laptops, smartphones, or tablets, to access the company’s network and applications. This model can reduce the costs and risks associated with managing and securing these devices, as the responsibility is shifted to the employees. However, BYOD also introduces some challenges, such as ensuring compliance with security policies, protecting sensitive data, and supporting different types of devices and operating systems.
COPE stands for Corporate Owned Personally Enabled, which is a deployment model that involves the company providing devices to its employees and allowing them to use them for both work and personal purposes. This model can give the company full control over the security and management of these devices, as it can enforce security policies, install software updates, monitor usage, and wipe data remotely. However, this model also increases the costs and risks associated with owning and maintaining these devices.
COBE stands for Corporate Owned Business Only, which is a deployment model that involves the company providing devices to its employees and restricting them to work-related use only. This model can ensure the highest level of security and compliance for these devices, but it also reduces the productivity and satisfaction of the employees, as they have to carry multiple devices for different purposes.
EMAIL SECURITY+ CHEAT SHEET
SPF (Sender Policy Framework), as it lets him specify which mail servers are authorized to send emails on behalf of the company’s domain.
DMARC (Domain-based Message Authentication, Reporting, and Conformance) uses the results of SPF and DKIM checks, it doesn’t directly list authorized servers for a domain.
DKIM (DomainKeys Identified Mail) provides validation of the domain name identity associated with a message through cryptographic authentication, but it doesn’t dictate authorized servers. IMAP (Internet Message Access Protocol) is utilized for retrieving emails from a server and isn’t designed to specify authorized sending servers for a domain.
DEV OPS SECURITY+ CHEAT SHEET
The SDLC (Software Development Life Cycle) methodically divides the software creation and maintenance process into specific phases. By doing so, it ensures that security considerations are integrated and prioritized from the start of software development through its maintenance.
CI/CD (Continuous Integration and Continuous Delivery) focuses on the frequent delivery of applications to customers by introducing automation into the stages of app development. Although it can incorporate security elements, its primary goal isn’t to segment software creation and maintenance like the SDLC.
While RAD (Rapid Application Development) emphasizes fast prototyping and speedy software delivery, it does not inherently focus on segmenting software creation into discrete security-focused phases as the SDLC does.
While Scrum is an Agile framework used in software development that emphasizes collaboration and adaptability, it doesn’t divide software creation and maintenance into discrete security-focused phases in the same manner as the SDLC.
ENCRYPTION SECURITY+ CHEAT SHEET
AES (Advanced Encryption Standard) is a symmetric encryption standard used to protect data at rest and in transit, ensuring confidentiality and security.
SHA (Secure Hash Algorithm) is a set of cryptographic hash functions designed to ensure data integrity, not to encrypt data.
HMAC (Hash-Based Message Authentication Code) is a specific construction for creating a message authentication code (MAC) involving a cryptographic hash function in combination with a secret key, rather than for encryption purposes.
RSA (Rivest-Shamir-Adleman) is an asymmetric encryption standard typically used for secure data transmission, not specifically for data at rest.
The RSA algorithm uses a trapdoor function, where encryption is easy to perform using the public key, but reversing the process (decryption) without the private key is challenging. RSA’s principle is that certain mathematical operations are easy to perform, but their inverse operations are difficult without specific knowledge.
WPA2-PSK leverages a passphrase to create a key, called the PMK, to encrypt communications. This is a distinguishing feature of WPA2’s personal authentication. The Dragonfly handshake is a key feature of the WPA3’s Simultaneous Authentication of Equals (SAE) method. This does not pertain to the WPA2 authentication mechanism.
ECC (Elliptic curve cryptography) is a type of trapdoor function that is efficient with shorter key lengths. For instance, ECC with a 256-bit key provides roughly the same security as RSA with a 2048-bit key. The primary advantage is that ECC has no known shortcuts to cracking it, making it particularly robust. Diffie-Hellman is an algorithm primarily for secure key exchange, not directly comparable to the encryption efficiency offered by ECC’s shorter key lengths.
Digital Signature Algorithm (DSA) is an algorithm used for digital signatures, but it doesn’t inherently offer the same efficiency in terms of key length as ECC. While a foundational asymmetric algorithm, RSA generally requires longer key lengths than ECC to achieve comparable security levels.
ECC (Elliptic Curve Cryptography) is a form of public key cryptography based on the algebraic structure of elliptic curves over finite fields primarily used for digital signatures and key exchanges. SHA-256 (Secure Hash Algorithm 256-bit) is a cryptographic hash function, not primarily used for digital signatures or key exchanges.
DES (Data Encryption Standard) is an older symmetric-key method of data encryption which was largely replaced due to vulnerabilities, focusing primarily on data encryption.
Twofish is a symmetric block cipher which, like AES, encrypts data in blocks using the same key for encryption and decryption.
Diffie-Hellman is an asymmetric cryptographic technique specifically designed for securely exchanging cryptographic keys over public channels, allowing two parties to generate a shared secret without having previously met.
Key exchange is a process in which two communicating parties establish a shared secret key, typically used for symmetric encryption. This key is established in a manner so that eavesdroppers, even if they intercept the key exchange messages, cannot determine the shared key. The most common method for key exchange is the Diffie-Hellman protocol.
Asymmetric encryption uses different keys for encryption and decryption, but it doesn’t involve the exchange of cryptographic keys. Symmetric encryption the same key for both encryption and decryption, but it doesn’t involve the exchange of cryptographic keys.
Hashing involves converting input data (often called a message) into a fixed-length string of bytes. It’s primarily used for data integrity checks and is not reversible, meaning you cannot retrieve the original input from its hash. Therefore, it isn’t suitable for the purpose of exchanging cryptographic keys or establishing shared secrets for communication.
RSA (Rivest–Shamir–Adleman) is an asymmetric encryption algorithm that uses two keys. A message that’s encrypted with the public key can only be decrypted with the private key, and vice versa.
AES (Advanced Encryption Standard) is a symmetric encryption method where the same key is used for both encryption and decryption, not involving distinct public and private keys.
HMAC (Hash-Based Message Authentication Code) is a specific construction for creating a message authentication code (MAC) involving a cryptographic hash function, but not a form of asymmetric encryption.
3DES (Triple Data Encryption Standard) is an evolved form of the older Data Encryption Standard (DES) which uses symmetric key algorithms for the encryption of electronic data, not involving public and private keys.
RISK MANAGEMENT SECURITY+ CHEAT SHEET
KRIs are metrics that provide early warnings of increasing risk exposures, enabling organizations’ leadership to manage these risks proactively.
A risk threshold is the defined level of risk an organization is willing to accept, not a predictive indicator.
Risk metrics are quantitative measures of risk but do not specifically refer to the predictive indicators used for monitoring potential risks.
Risk parameters are specific variables used within risk assessment processes, not predictive indicators.
The risk management strategy of AVOID aims to eliminate the risk entirely by avoiding activities or situations that may expose the organization to potential threats.
The risk management strategy of ACCEPT involves acknowledging and tolerating the risk without taking additional measures to mitigate it. It is usually appropriate when the cost of mitigation outweighs the potential impact of the risk.
The risk management strategy of MITIGATE involves taking actions to reduce the impact or likelihood of a risk occurring. This can include implementing security measures, contingency plans, or redundancy to minimize the consequences of the risk.
A RISK MATRIX is a visual tool used to determine the severity and likelihood of risks, not the acceptable variance in investment performance. While the firm’s decision to have a high-risk investment portfolio at all does reflect its risk appetite, the question specifically refers to the acceptable variance, which is the risk tolerance.
RISK OWNER is tasked with the ongoing management and mitigation of risks pertaining to the data management platform.
RISK REGISTER would be the tool Sarah uses to track and assess the risks, not her role.
RISK INDICATOR would be a metric to monitor and assess risk levels
RISK ASSESSOR might be a role taken on when evaluating risks, but it does not encapsulate comprehensive management responsibilities.
RISK TOLERANCE refers to an organization’s predetermined level of acceptable risk exposure. It represents the extent to which an organization is willing to tolerate potential risks before taking action to mitigate or avoid them.
The exposure factor is a calculation that determines the amount of value that is lost if an event takes place. It doesn’t measure an organization’s level of acceptable risk exposure. The term “conservative” is not directly related to risk management. In financial contexts, it may refer to a risk-averse approach or cautious decision-making.
Risk indicators are specific metrics used to monitor and assess the level of risk in an organization, but they do not directly involve identifying responsible parties.
Impact specifically refers to the magnitude of the consequences if a risk event occurs, typically assessed in terms of financial loss, operational disruption, or other forms of damage.
Risk appetite refers to an organization’s willingness to take on risk in pursuit of its business objectives. It reflects the organization’s strategic approach to risk and how much risk it is willing to undertake to achieve specific goals.
Risk deterrence involves taking measures to reduce or mitigate the impact of an event. In this case, they aren’t evaluating the impact or taking measures to reduce the likelihood of a specific event.
The recovery point objective (RPO) is the maximum amount of data loss an organization is willing to tolerate. It defines the point in time to which systems and data must be recovered after a disruption.
The mean time to repair (MTTR) is the average time taken to repair a system or component after a failure or disruption.
The recovery time objective (RTO) is the maximum acceptable downtime for a system or process to be restored and functioning after a disruption.
The mean time between failures (MTBF) is the average time interval between failures of a system or component.
PORT SECURITY+ CHEAT SHEET
Port 1433 is the default for Microsoft SQL Server. Organizations typically restrict or monitor access to this port to prevent unauthorized database operations.
Domain Name System (DNS) uses port 53 for resolving domain names into IP addresses. It isn’t associated with database operations.
Port 443 is used for secure web traffic through SSL/TLS. It’s not directly related to database queries.
File Transfer Protocol (FTP) uses port 21 for unencrypted data transfers, not for database operations.
BACKUPS SECURITY+ CHEAT SHEET
Frequency refers to how often data backups are carried out.
Regular backups at set intervals are crucial to minimize the potential loss of data. Replication is the copying of data from one system to another. The regularity with which this is done, isn’t an important part of replication.
Journaling entails verifying and logging data, not the regularity of backups. While load balancing is a technique for distributing workloads across multiple computers or networks, it doesn’t relate to how frequently backups are created.
PUBLIC KEY INFRASTRUCTURE SECURITY+ CHEAT SHEET
Key escrow refers to the secure storage of cryptographic keys, ensuring they can be accessed under specific conditions, but it’s not directly used to encrypt or decrypt messages.
A private key is kept secret by its holder and is used to decrypt messages that are encrypted with its corresponding public key. It’s not used by external entities to encrypt messages to the key holder.
VULNERABILITY SCANNING SECURITY+ CHEAT SHEET
A critical classification is assigned to vulnerabilities that, if exploited, would cause significant damage, have a high likelihood of being exploited, or expose sensitive data. These should be addressed immediately.
Medium vulnerabilities pose a moderate risk and usually have some mitigating factors that lessen their potential impact or likelihood of exploitation.
Informational vulnerabilities are typically findings that don’t pose any immediate risk but are documented to provide a complete view of the assessment.
Low vulnerabilities have minimal potential damage and are less likely to be exploited. They are of lesser priority compared to other classifications.
National legal implications are laws and regulations set at the country level that outline the requirements and boundaries for data protection and privacy.
ACCESS CONTROL SECURITY+ CHEAT SHEETS
Discretionary Access Control (DAC) is an authorization model where the owner of the resource decides who is allowed to access it.
Mandatory Access Control (MAC) is an authorization model where access to resources is determined by a set of rules defined by a central authority.
Role-Based Access Control (RBAC) is an authorization model that assigns permissions to roles, rather than individual users.
Attribute Based Access Control (ABAC) determines access through a combination of contexts and system wide attributes.
AUDITS AND ATTESTATIONS SECURITY+ CHEAT SHEET
Attestation is the term that refers to the process of affirming the accuracy and completeness of compliance reports. It involves providing formal statements or declarations about the organization’s compliance with specific regulations or standards. Attestation can be done internally by the organization’s management or externally by a third-party auditor.
An independent third-party audit involves an external and unbiased assessment conducted by an independent auditor or a third-party organization. The purpose of this audit is to provide an objective evaluation of the organization’s compliance status. Independent third-party audits are often used to validate and verify compliance claims made by the organization and can offer more credibility to compliance reports.
Internal assessment involves the organization’s internal evaluation of its adherence to established compliance requirements. This process may include self-assessments, internal audits, and reviews conducted by the organization’s compliance team to ensure that it meets the necessary regulatory and security standards.
A regulatory examination is an external evaluation conducted by a government agency or a regulatory body to ensure that an organization is complying with specific regulations or industry standards. During a regulatory examination, the organization’s compliance practices, controls, and processes are thoroughly reviewed to assess their alignment with the applicable rules and requirements.
ZERO TRUST SECURITY+ CHEST SHEET
The policy engine is responsible for making access control decisions based on pre-defined policies and contextual information about the subject/system.
The policy administrator is responsible for defining and managing the access control policies used by the policy engine.
The subject/system refers to the entity (user or device) that is requesting access to a resource. The policy enforcement point is responsible for enforcing the access control decisions made by the policy engine.
The Policy Enforcement Point (PEP) is responsible for ensuring that security policies are enforced when a user or device tries to access resources on the network. It acts as a gatekeeper, verifying the identity and context of the access request against the policies set by the organization before allowing or denying access.
Policy-driven access control entails setting permissions based on organizational roles or requirements. For instance, ensuring HR personnel only have access to payroll systems embodies this principle. Mandatory access control assigns security labels on information and grants access based on those labels.
SUPPLY CHAIN SECURITY+ CHEAT SHEET
VENDOR SELECTION is the process of evaluating and choosing vendors based on various criteria, including their alignment with the organization’s ethical and legal requirements.
VENDOR MONITORING refers to continuously evaluating a vendor’s security performance and compliance with contractual requirements, but it does not directly relate to ethical and legal criteria. It occurs after the vendor is chosen.
VENDOR ASSESSMENT involves evaluating the security measures and vulnerabilities of a vendor’s systems and infrastructure, but it does not specifically focus on ethical and legal requirements. It occurs after the vendor is chosen.
A MASTER SERVICE AGREEMENT (MSA) is precisely designed to establish the overall framework for a long-term business relationship between an organization and a vendor. It provides a foundation for future agreements and contracts by outlining general terms, conditions, and responsibilities. It generally is concluded after a vendor is chosen.
A Work Order (WO) or Statement of Work (SOW) is a document used to specify the specific tasks, deliverables, and timelines for a particular project or service. It is not intended to establish an overall framework for a long-term relationship.
A Service-level Agreement (SLA) typically outlines specific performance metrics, service levels, and responsibilities for ongoing services, rather than establishing an overall framework for a long-term relationship.
A Memorandum of Understanding (MOU) is a non-binding document used to express mutual understanding and intentions between parties. It is not typically suitable for establishing a formal framework for a long-term business relationship.
RACE CONDITIONS SECURITY+ CHEAT SHEET
A TOC vulnerability occurs when an attacker exploits the time gap between the verification of data and its use, potentially leading to unauthorized or malicious activities.
MEMORY LEAKS are when a program doesn’t release memory that it no longer needs, leading to potential system slowdowns or crashes. This does not involve data manipulation after verification.
RACE CONDITIONS relate to the unexpected order and timing of events in software execution but are not specifically about the gap between data verification and use.
RESOURCE EXHAUSTION refers to the overuse of system resources, be it CPU time, memory, or others, which can lead to denial of service. It’s not specific to data manipulation after its verification.
Time-of-use (TOU) is a type of race condition that occurs when a process performs an action on a resource without verifying that it is still in the same state or value as when it was last checked. It can lead to incorrect or unauthorized actions based on invalid assumptions.
BUFFER OVERFLOW is a type of memory corruption that occurs when a program writes more data than the allocated buffer can hold, causing it to overwrite adjacent memory locations. It can lead to crashes, code execution, or privilege escalation.
MEMORY INJECTION is the insertion of malicious code into a system’s memory, not the exploitation of a time gap between a check and use of a condition.
CYBER KILL CHAIN SECURITY+ CHEAT SHEET
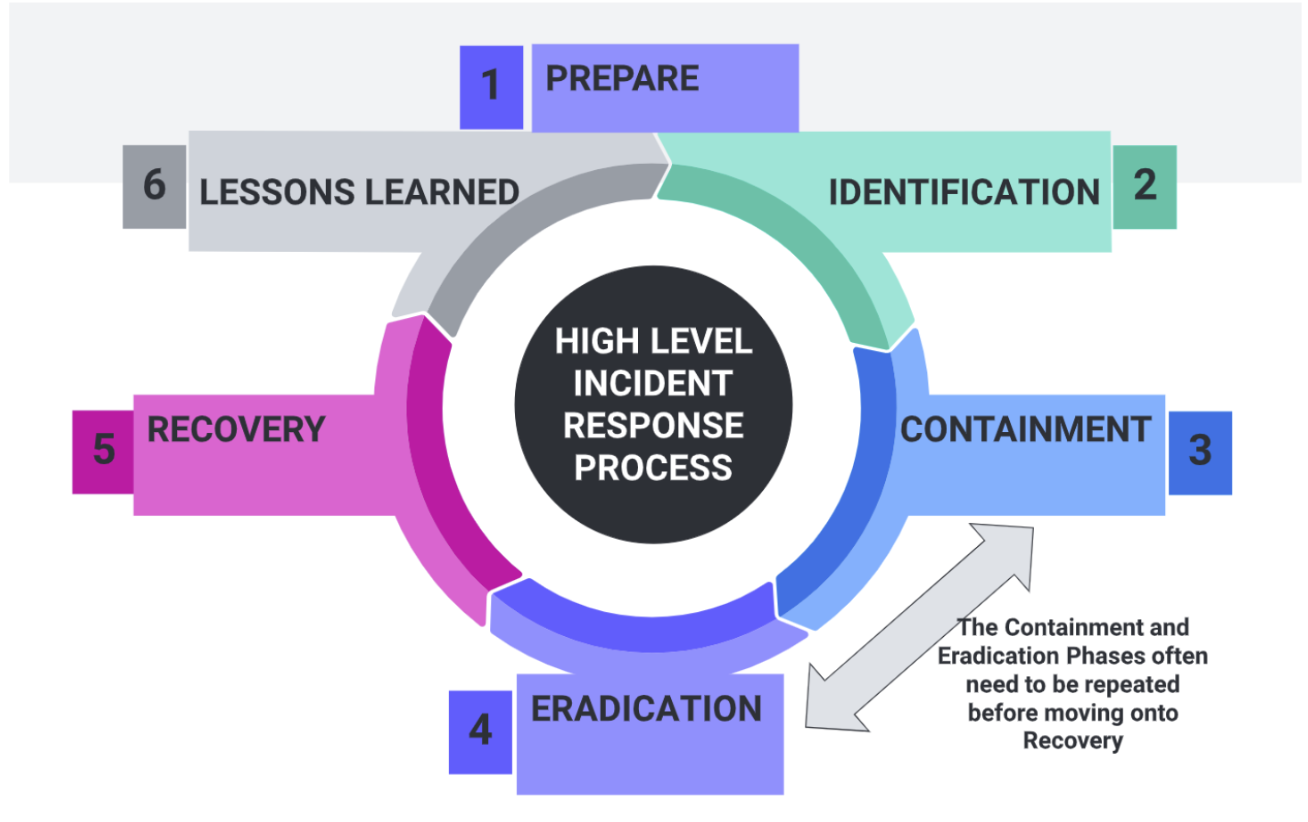
The ERADICATION PHASE in the incident response process involves removing the root cause of the incident from affected systems and networks to prevent its recurrence. This phase is crucial to ensure that the incident does not resurface and cause further damage to the organization.
Analyzing the evidence and determining the root cause of the incident falls under the ANALYSIS PHASE of the incident response process. This phase comes after containment and aims to understand how the incident occurred and what vulnerabilities were exploited.
Identifying and classifying incidents based on their severity and impact to the organization is part of the DETECTION PHASE in the incident response process. This phase involves recognizing that an incident has occurred and understanding its potential implications.
Developing an incident response plan, defining roles and responsibilities, and conducting regular training and drills belong to the PREPERATION PHASE of the incident response process. Part of this phase involves brainstorming and considering what can be done if a security problem occurs. This phase ensures that the organization is ready to respond effectively to incidents, but it does not directly involve eradicating the root cause of a specific incident.