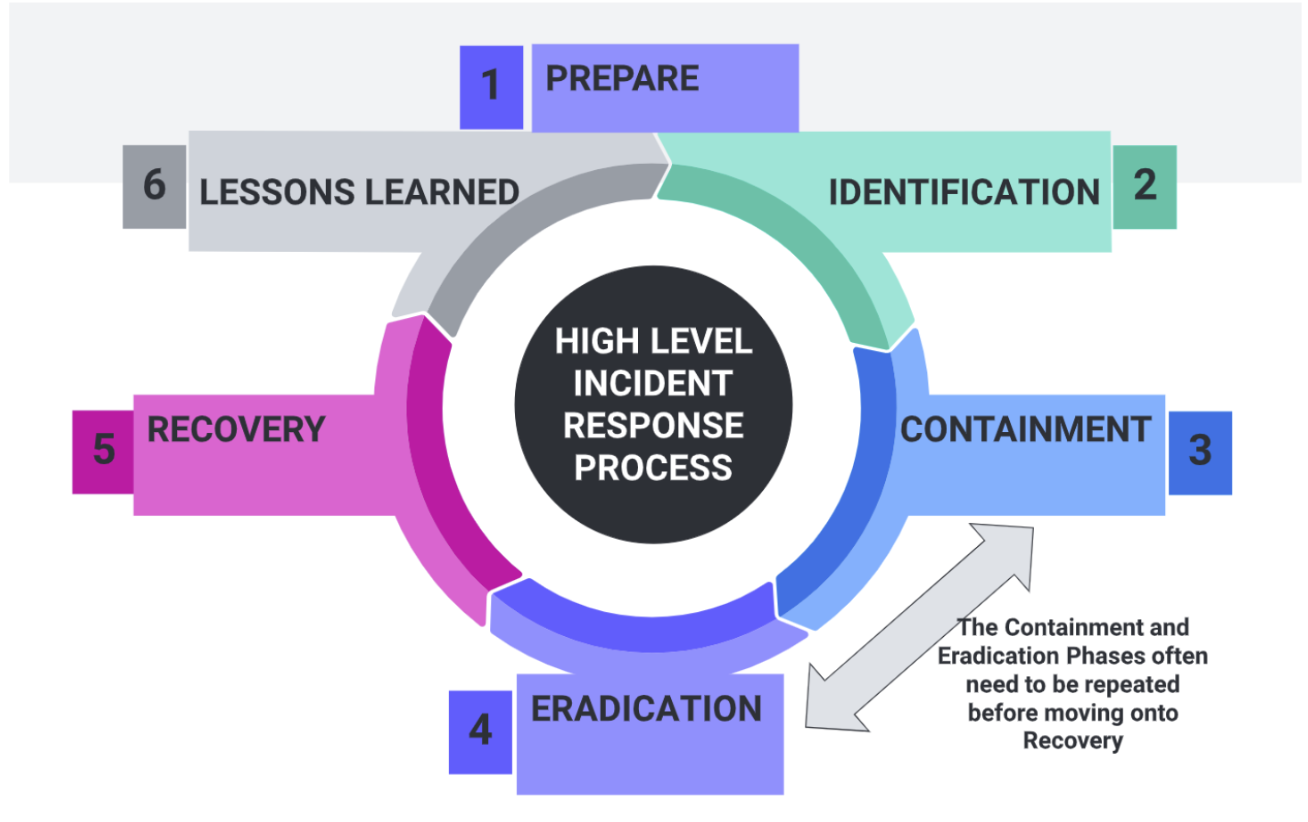
For the Incident Response Plan to be executed, a certain threshold of severity needs to be reached: when the incident has the potential to inflict a critical impact on business operations and is caused by an unauthorised group or individual, whether external cyber criminal syndicates or an insider attack by an employee.
An incident on the other hand has the following hallmarks:
- Any suspicious activities that are picked up by the IPS or discovered in the operating system event logs monitored in Syslog and the company’s SIEM software have to be reported to the Chief Security Officer or his/her delegate.
- The plan should not be evoked during an ‘event’ that is technical in nature such as network hardware failure or a blackout on the company cloud.
3.1. Incident Response Form
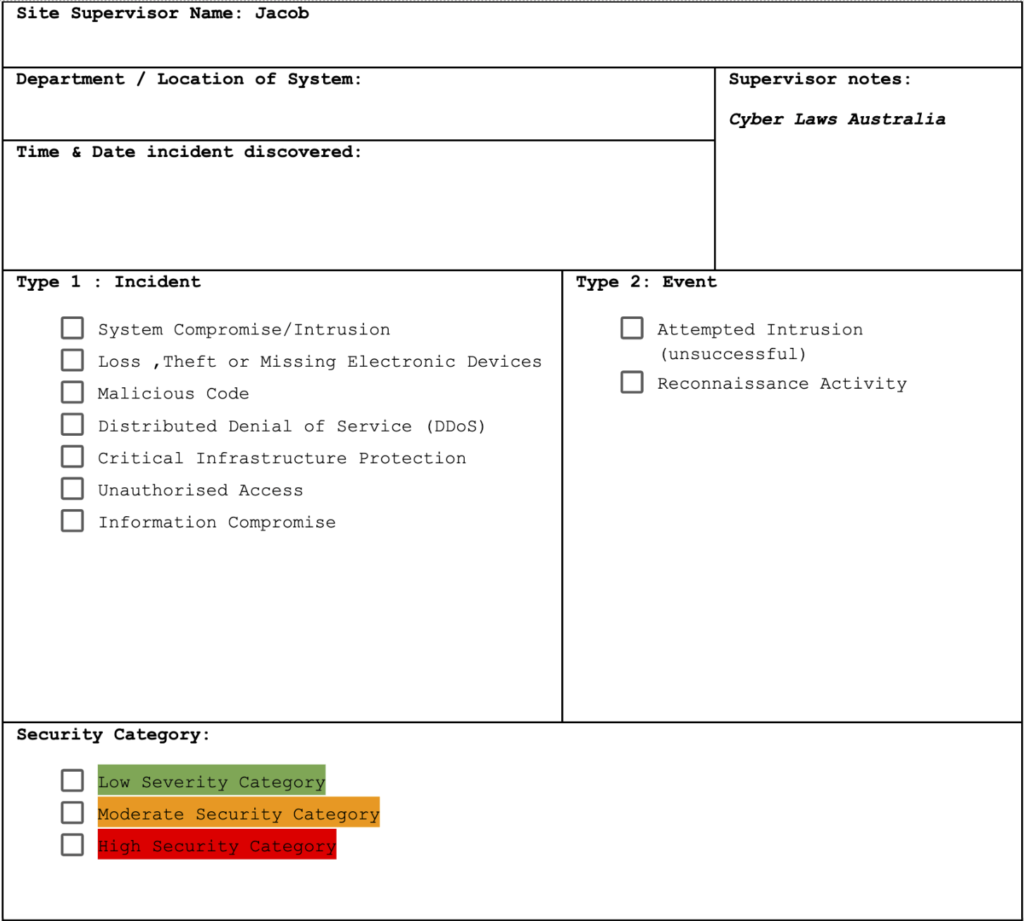
To standardise the Incident Response, printed copies of Incident Response Form 1 have been distributed to all departments of XYZ Company.
- The supervisor in charge of the department where the incident occurs is to fill out the Incident Response Form 1 attached below and immediately forward it to the Chief Security Officer to determine whether it reaches the critical threshold to declare an incident.
- Incident Response Form 1
3. Invoking the Incident Response Plan
For the Incident Response Plan to be executed, a certain threshold of severity needs to be reached: when the incident has the potential to inflict a critical impact on business operations and is caused by an unauthorised group or individual, whether external cyber criminal syndicates or an insider attack by an employee.
An incident on the other hand has the following hallmarks:
- Any suspicious activities that are picked up by the IPS or discovered in the operating system event logs monitored in Syslog and the company’s SIEM software have to be reported to the Chief Security Officer or his/her delegate.
- The plan should not be evoked during an ‘event’ that is technical in nature such as network hardware failure or a blackout on the company cloud.
3.1. Incident Response Form
To standardise the Incident Response, printed copies of Incident Response Form 1 have been distributed to all departments of XYZ Company.
- The supervisor in charge of the department where the incident occurs is to fill out the Incident Response Form 1 attached below and immediately forward it to the Chief Security Officer to determine whether it reaches the critical threshold to declare an incident.
- Incident Response Form 1
The Incident Response Plan is part of a broader Business Continuity Plan that contains a business impact analysis and risk management plan to help identify and treat most of the risks to the business. The following is a list of supporting Standard Operating Procedures (SOPs) available on the company cloud and in physical print form to support our organisation’s Incident Response Plan:
- Crisis management Plan ( example: https://aws.xyzcompany/crisis-management-plan.pdf)
- Business Continuity Plan (example: https://aws.xyzcompany/crisis-management-plan.pdf)
- Disaster Recovery Plan (example: https://aws.xyzcompany/crisis-management-plan.pdf)
The Incident Response Team and Senior Executive Management have access to all three plans.