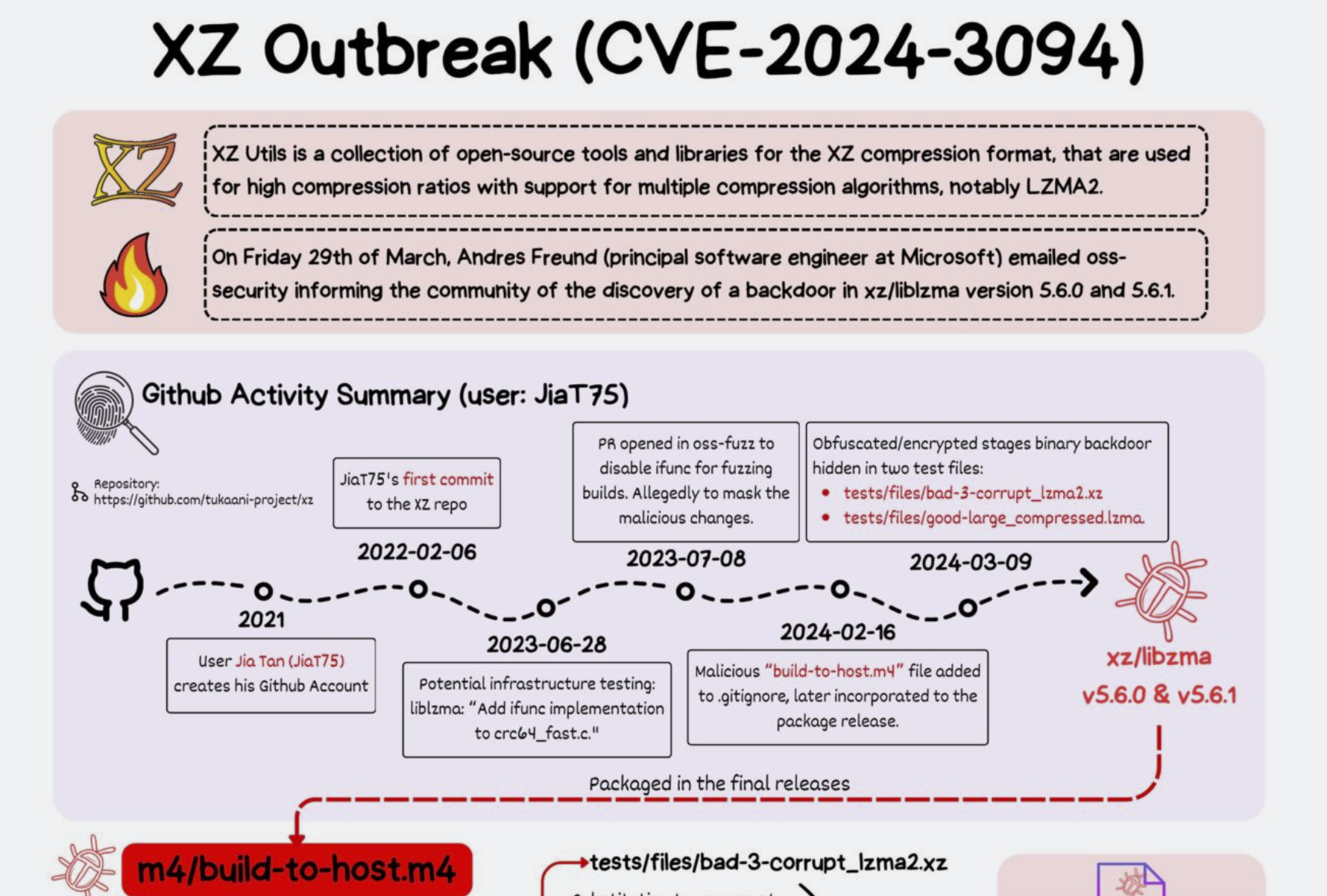
In the leadup to the easter long weekend, Andres Freund, a software engineer at Microsoft, was testing an unstable Debian release (nicknamed “sid”) shortly before it was due to be released when he noticed something strange: SSH logins that allow users to remotely enter the operating system were chewing up CPU juice and spitting out errors. After a little digging he discovered the liblzma data compression library, part of the popular XZ utility package, was compromised: “the upstream xz repository and the xz tarballs have been backdoored.”
Red Hat warned the XY Utilz vulnerability, designated CVE-2024-3094, “enable a malicious actor to break sshd authentication and gain unauthorized access to the entire system remotely.” It futher advised users to discontinue usage of “Fedora 41 of Fedora Rawhide for work or personnel use” and noted the vulnerability affeccted include “Kali Linux, openSUSE Tumbleweed, openSUSE MicroOS, and Debian testing, unstable and experimental versions.”
The alias behind the attack–Jia Tan on Github–spent two years building bonafides and expanding their network and grooming colleagues with social proof by receiving vouches from at least five others. The years-long patience required to groom colleagues in the not-for-profit open source community has led experts to believe this was the work of a nation state: “That type of human-enabled digital spycraft is nearly unprecedented in open source, argued Anjana Rajan, the assistant national cyber director at the White House Office of the National Cyber Director. ‘This is like an insider threat in the open source ecosystem, which we haven’t really seen before’
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has advised Linux administrators to roll back XZ Utils to an uncompromised version earlier than 5.6.0.
Edit on the Aftermath of CVE-2024-3094: A press release from U.S. Commerce Department’s National Institute of Standards (NIST) has revealed a growing backlog of vulnerabilities is submitted to the National Vulnerability Database (NVD) and “requiring analysis”. The institute analyzed only 199 of 3370 CVEs it received last month stating “Currently, we are prioritizing analysis of the most significant vulnerabilities.”
This month another 677 potential vulnerabilities were submitted to the NVD of which only 24 have been analyzed. The NVD includes a standard-based CVSS severity scores, impacted software and platforms, contributing weaknesses, and links to patches. NIST, which had its budget cut by almost 12% this year, called the NVD “a key piece of the nation’s cybersecurity infrastructure,” adding that “We are also looking into longer-term solutions to this challenge, including the establishment of a consortium of industry, government and other stakeholder organizations that can collaborate on research to improve the NVD.”